Layer 8 Security
Layer 8 Security | 1,985 followers on LinkedIn. Solving data risk management challenges with practical security, compliance, and privacy strategies. | Layer 8 Security is a cybersecurity consulting, advisory, and technical services company that creates risk management solutions for your evolving information security and compliance needs. Today’s business environment requires seamless integration with third-party vendors, clients, and partners. We ensure your information ecosystem is secure, compliant and resilient to the severity and frequency of a disruption resulting from a cyber attack.
Layer 8 Security is a cybersecurity consulting, advisory, and technical services company that creates risk management solutions for your evolving information security and compliance needs. Today’s business environment requires seamless integration with third-party vendors, clients, and partners. We ensure your information ecosystem is secure, compliant and resilient to the severity and frequency of a disruption resulting from a cyber attack.
The Layer 8 Security philosophy is focused on the human layer of cybersecurity. where business processes and technology intersect. As the cyber threats evolve in sophistication so must the defenses of companies, starting with its people. We are passionate about what we do. We refer to ourselves as Sheep Dogs; we feel a benevolent call to help others.

Layer 8 Security - Securing the Nut Between the Keyboard & Screen

Enabling Technologies and Architecture for 5G-Enabled IoT

BrianLangley, Author at Layer 8 Security

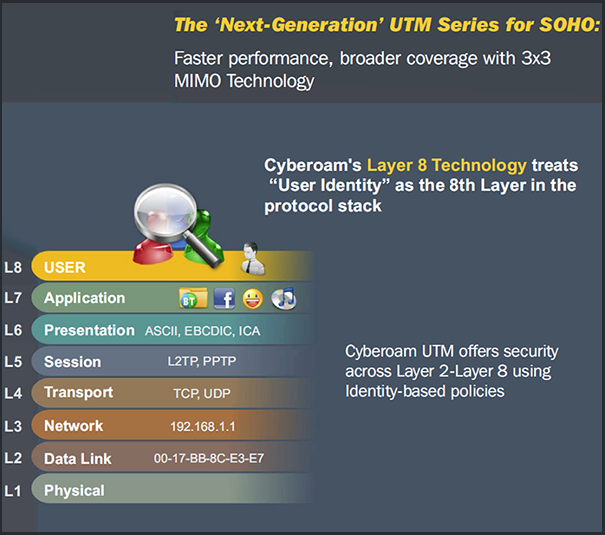
Cyberoam awarded patent for Layer-8 security method – Upgrade Magazine

Philadelphia Business Journal Veterans of Influence Rising Star Awards 2022: Sean Toolan, Layer 8 Security - Philadelphia Business Journal

ZeroEyes Achieves ISO/IEC 27001:2013 Certification, Confirming Integrity of Information Security Management System

Layer 8 Security – Página Oficial
Cyberoam CR2500iNG-XP

Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

Layer 8 Security - Securing the Nut Between the Keyboard & Screen