
Solved 2 - Configure the perimeter to the secure network
4.7
(398)
Write Review
More
$ 11.50
In stock
Description
Solved] 1.1 Configure Interfaces and Zones Complete the following

What is VLAN? Types, Advantages, Example

Perimeter Device - an overview

Perimeter Network - an overview

Network Design Scenario #2: DMZ Design
Solved 2 - Configure the perimeter to the secure network
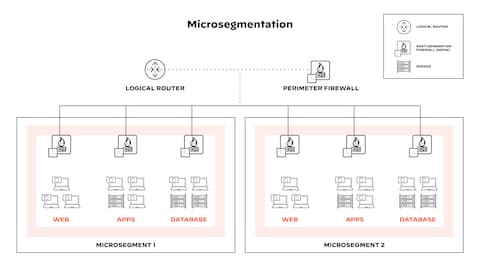
What Is Microsegmentation? - Palo Alto Networks

Secure Connectivity from Public to Private: Introducing EC2 Instance Connect Endpoint

What Is Firewall: Types, How Does It Work & Advantages
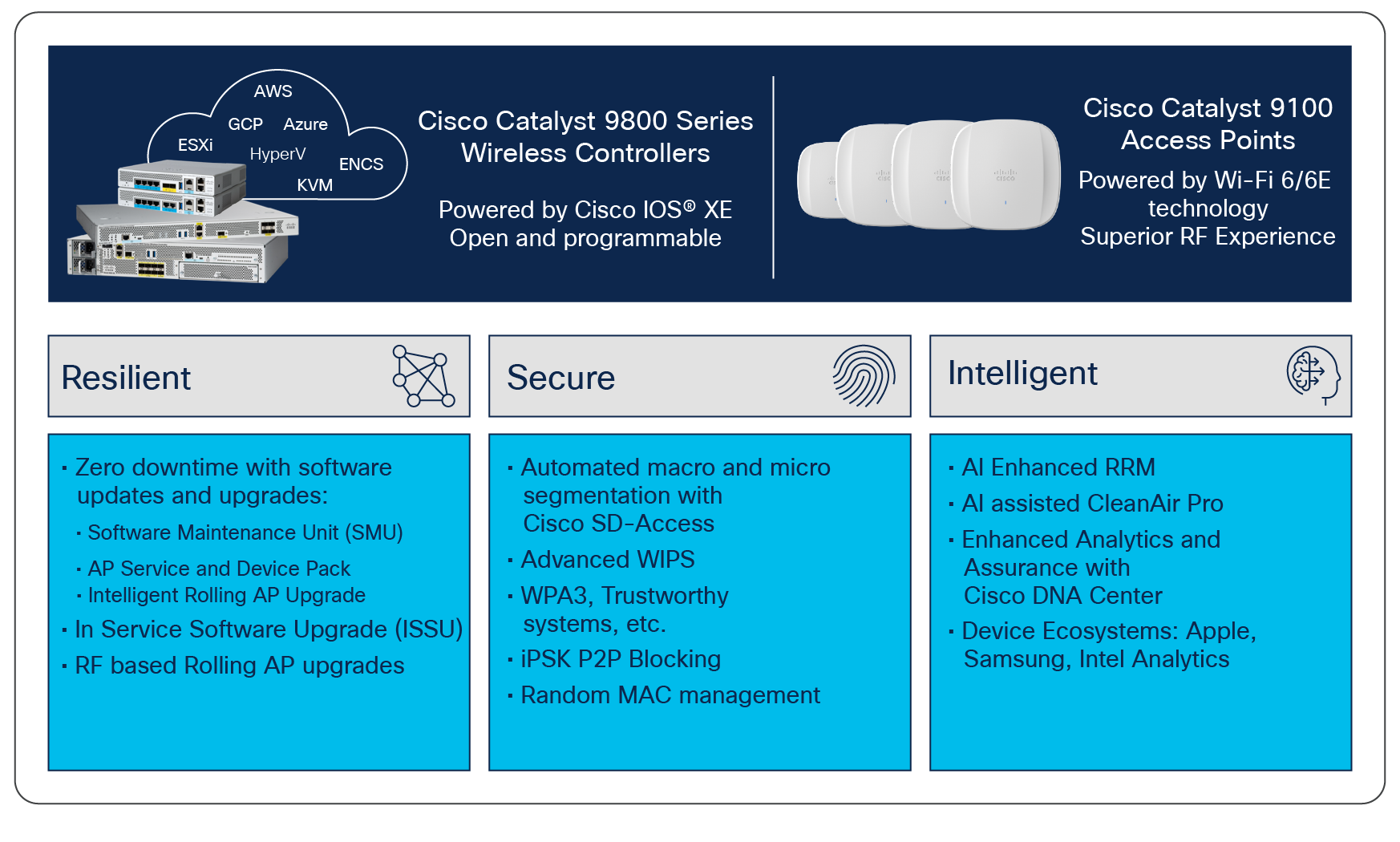
Cisco Catalyst 9800 Series Configuration Best Practices - Cisco

How to Set Up and Optimize Your Wi-Fi Router for the Best Performance

Network Design: Dual ISP, DMZ, and the Network Edge
Related products
You may also like








