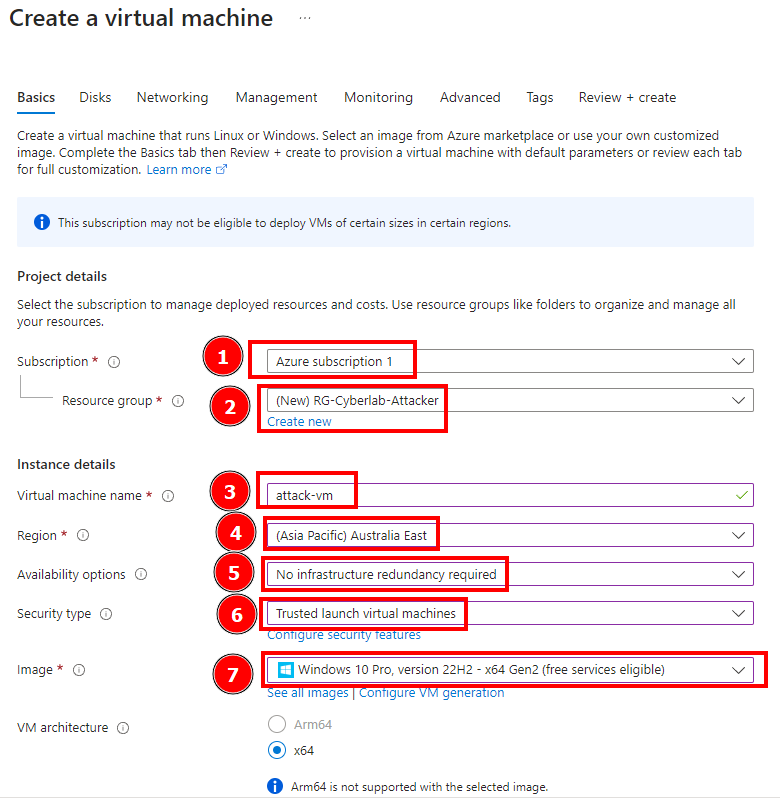
Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui
In this session we’re going to simulate an attack from another VM and then observe the attacker’s log. First we create an attacker VM. This VM’s name is attack-vm and also contain a different…

How to Detect and Analyze DDoS Attacks Using Log Analysis

An Approach to Prevent DDoS Attack Using Real-Time Access Logs Analysis

Part 5: Configuring/Collection Windows Security Event Logs and Syslog Logs and for Log Analytics Workspace., by Duyet Bui

Log Analytics Agent error: The workspace key could not be validated

Part 9: Microsoft Sentinel Incident Response., by Duyet Bui

Portswigger: Exploiting vulnerabilities in LLM APIs

Attack Graph Response to US-CERT Alert (AA22-174A): Malicious Cyber Actors Continue to Exploit Log4Shell in VMware Horizon Systems - AttackIQ

Public Exploit Available for Critical VMware Bug CVE-2022-31656 - Security Investigation
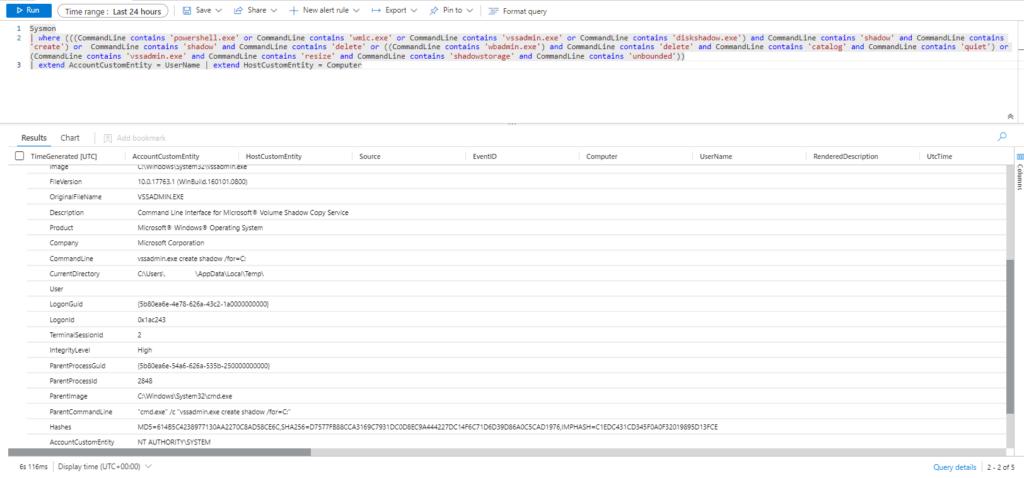
Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte 1 (ATT&CK T1003) – Red-Orbita

Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui

Scenario based attack simulation » 2
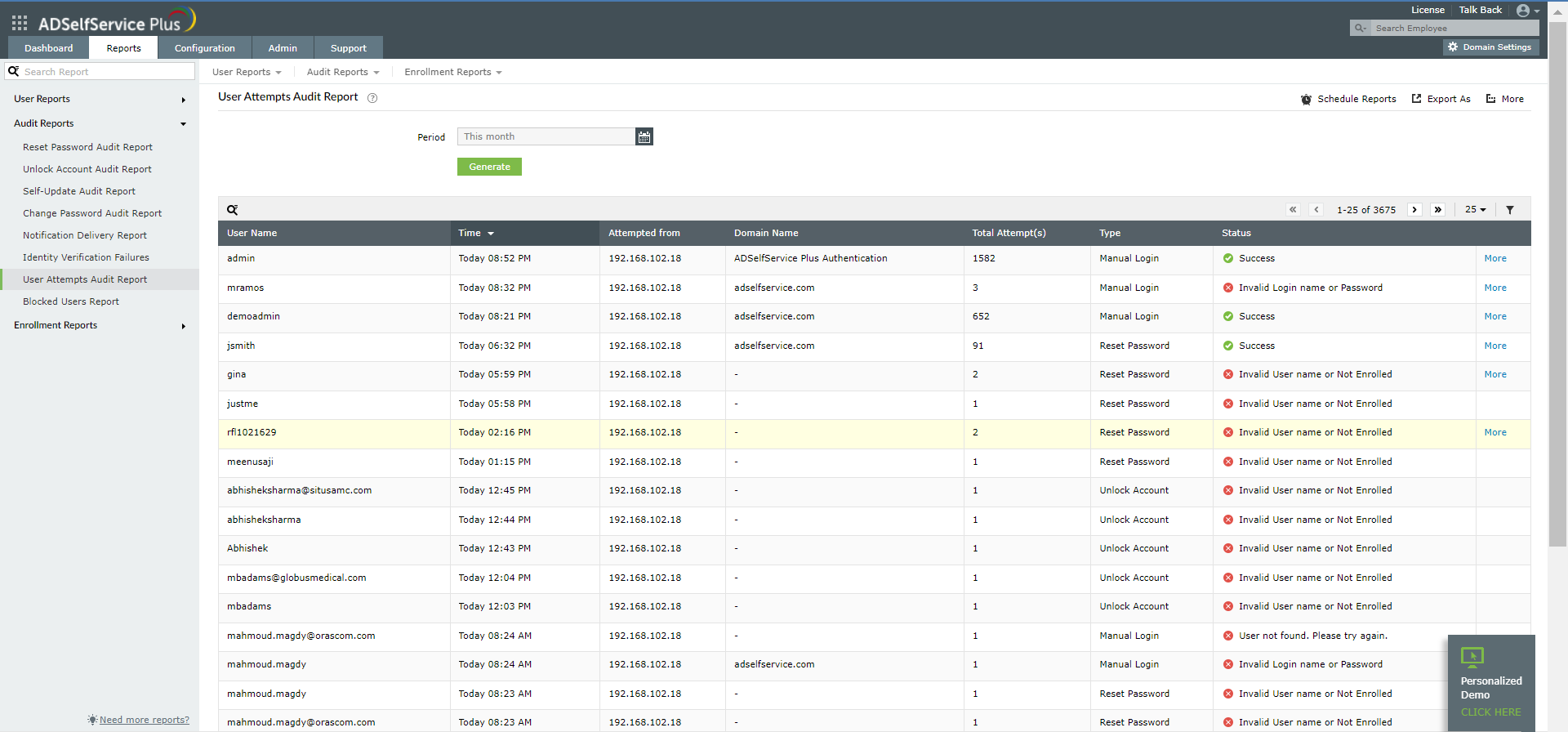
Identify and Prevent Brute Force Attack.

Session Misconfiguration Attack Exploitation process.

PDF) POIROT: Aligning Attack Behavior with Kernel Audit Records for Cyber Threat Hunting
Log Validation with Attack Simulation